Introduction to laptop security
Laptops are a staple of modern organizations. They’re an essential tool for businesses and workers, and they’re a great way to stay connected. But they also represent one of the greatest security risks that businesses and employees face.
Why are laptops such a big security risk?
The main reason that laptops are such a big security risk is that they can be easily compromised. A typical laptop has many different ways it can be hacked into:
They often have vulnerabilities in their operating systems or software (like Windows). They often use default passwords that can be easily guessed by hackers. They often have ports which allow remote access to the internet via USB or Bluetooth connections (in order to connect other devices). And they often have apps downloaded onto them which allow hackers to access sensitive data stored on them (like email accounts, passwords etc).
The top 5 security threats laptops present in the enterprise:
1 – Phishing Attacks
A phishing attack is an attempt to obtain sensitive information such as usernames, passwords and credit card details (and sometimes indirectly, money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication. An email that appears to be from a known or trusted source but is actually from an unknown or untrusted source is known as “spear phishing”.
2 – Hacking Attempts
A hacking attempt is any activity that attempts to gain unauthorized access to a computer system. Laptops, which are often used outside of the office, are a prime target for hackers. They’re more vulnerable because they’re portable and tend to contain sensitive information.
3 – Insider Threats
An insider threat is any person who has been granted access to an organization’s resources and intentionally uses those resources for malicious purposes. This can include employees, contractors, suppliers, customers or anyone with authorized access to a business’s network.
4 – Theft or Loss
Theft or loss of laptops can cause significant damage to your company because it contains sensitive and confidential information that should not be accessible by unauthorized persons. In addition, there may be legal implications if the laptop was stolen from an employee’s home and you did not have appropriate security measures in place.
5 – Network Perimeter and Endpoint Security
The first layer of protection is network perimeter security (NPS). This could be something like a firewall or VPN. It should help prevent unauthorized access to your data and prevent attacks like phishing attempts or man-in-the-middle attacks where someone intercepts data as it travels between two systems.
Endpoint security (ENS) is software that runs on your device to protect against malware, viruses and other threats. For example, most antivirus products offer ENS features that scan files before they’re opened or sent out over the internet in order to block malicious programs from entering your system. A good ENS product will also monitor your computer’s memory for suspicious activity and alert you if anything unusual happens with your computer’s processes or files (such as when a hacker tries to install malware onto your machine).
Even post-COVID many workers are not returning to company offices. In the U.S., 59% of employees working from home during the pandemic say they prefer to work remotely. Some companies have already announced they are switching to a permanent remote workforce, making adequate network perimeter and endpoint security critical moving forward.
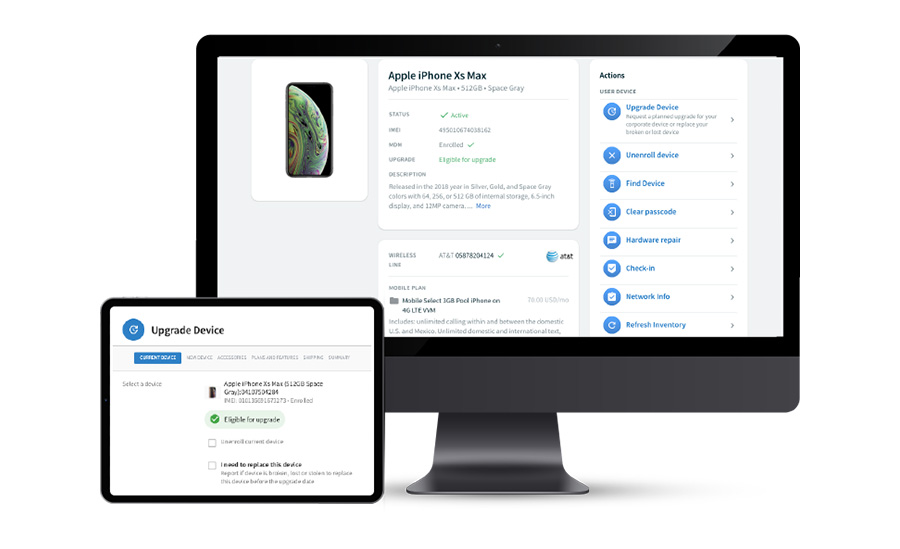
The Solution: Unified Endpoint Management
Tame your unmanaged devices
Unmanaged devices are a major security risk that can lead to costly data breaches and productivity loss. brightfin helps you gain visibility into all your corporate devices, whether they’re on-premises or mobile.
Securely deploy new devices with ease
Deploying new laptops is a time-consuming process that involves manual steps like creating accounts, installing software and configuring settings. Automate this process with a unified endpoint management (UEM) solution that simplifies the setup process for new devices and enables you to deploy them across multiple platforms.
Stay up-to-date with patches & OS upgrades
It’s important to update your OS regularly to ensure you have the latest security patches installed and that your company is protected from hackers who may be targeting known vulnerabilities within a particular software version. A UEM solution makes it easy for admins to quickly check which patches need to be installed across their entire fleet of laptops, desktops and tablets so they don’t miss critical updates due to lack of time or resources necessary for manual tracking.






