You’ve heard of BYOD, but what’s COPE?
If you’re an IT manager, there are probably several things that annoy you. One is perhaps the frequency of receiving password reset requests. A close second in the annoying-ness list is probably managing a growing number of devices on the network. Part of what makes endpoint management so hard is the sheer volume of mobile endpoints to juggle. Every second – 127 new IoT devices are connected to the web, and during 2020, experts estimate the installation of 31 billion IoT devices! Besides managing the devices themselves – smartphones, tablets, laptops, etc. – IT is also responsible for securing the users, apps, and data connected to those devices! It’s enough to make your head spin.
So, are there tips and tricks for making mobility management easier? Is BYOD now the only relevant device management model out there? Are there other options that bring added security? Let’s dive into some of the most popular device ownership models and some mobile solutions so that your organization can take its mobility infrastructure to the next level.
BYOD – Accessing sensitive corporate data alongside TikTok
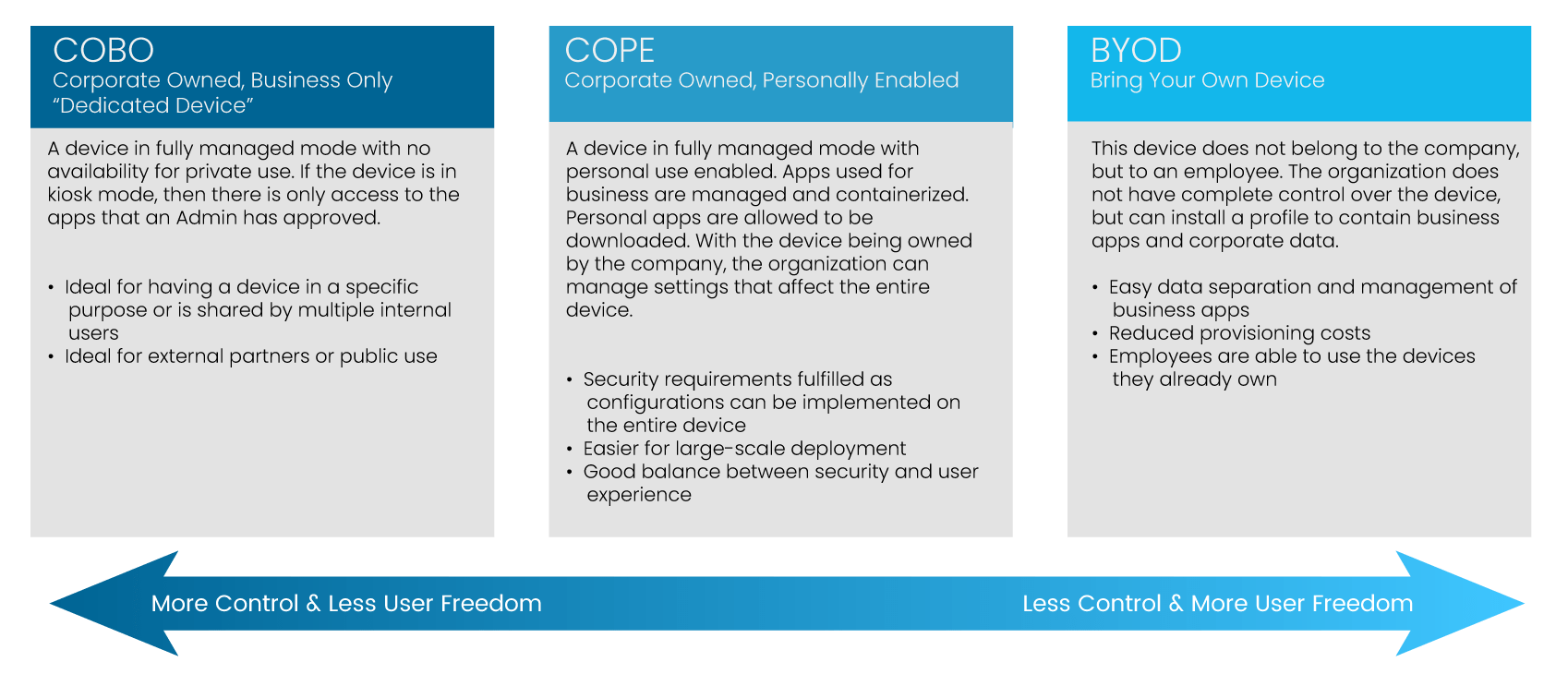
BYOD is one of the most well-known management frameworks and device ownership models in the enterprise. BYOD is so popular because it affords companies and employees ultimate flexibility – keeping corporate operational costs low and allowing employees to bring personal mobile devices into the workplace. The flip side of this flexibility level is employees may be accessing sensitive corporate content, right alongside creating TikTok videos or visiting their Instagram account. Even though business data and resources are accessed and stored on the phone, there’s usually limited security protocols in place in a BYOD environment. These risks can come from hackers or other scammers, or exposure can also happen when a phone is lost or stolen.
What about COBO?
On the other end of the device ownership spectrum is COBO. COBO stands for a company-owned, business-only type of device environment. With this scenario, devices are procured and owned by the company, meaning corporate IT monitors and secures those endpoints. These business-only devices prevent employees from accessing consumer or personal apps. Industries with field workers, where individuals require remote access to corporate applications, often rely on a COBO model. Companies can essentially ‘lock-down’ the mobile endpoint to keep data and apps secure. The downside is the additional costs put on corporations to buy and maintain devices and apps on behalf of employees.
What about COPE?
You might be asking – is there another option? Enter: COPE or a company-owned and personally-enabled device environment. In this arrangement, enterprises procure and provision devices for the business environment, but they are also available for personal use. One significant advantage of the COPE model is that organizations can provide all devices with business applications and resources centrally. Employees are then free to use their devices as they see fit. However, the device is operating in a secure framework from the get-go.
Security options for BYOD and COPE?
Which device environment is better for security – BYOD or COPE? Like most things in life, it depends! But, in most cases, larger organizations tend to adopt COPE because it brings the highest control and authority over the mobile ecosystem. For organizations dealing with thousands of devices, repairs, and replacements, there are also advantages to standardized tools in a COPE environment. Organizations with many compliance requirements, such as finance or healthcare, also benefit from COPE’s consolidated security approach. On the other hand, organizations may feel that BYOD brings flexibility and that more freedom can positively impact employees’ productivity and creativity.
Put your mobile strategy into action
In BYOD and COPE device environments, it is possible for IT teams to secure devices, apps, and data, using a Mobile Device Management (MDM) platform. MDM brings streamlined and centralized security with a single system of device management across the entire mobile environment. Using MDM, IT can set up apps, settings, and security configurations to protect all endpoints. Have questions about securing BYOD, COPE, or other device ownership models? Want help weighing the pros and cons of each? We love to talk BYOD, COPE, MDM, and other tech acronyms that can help make companies more secure.